Colleen Schnettler
March 21, 2024
AWS Setup for HelloQuery
If you’d like to connect an AWS RDS database on a private VPC to HelloQuery, there are a few additional steps you’ll have to take to whitelist our IPs.
Table of Contents
Make your db publicly accessible
The initial step in establishing a connection between your AWS RDS instance and HelloQuery involves configuring your database to be publicly accessible. This configuration does not expose your database to the public internet indiscriminately but is necessary for specifying more granular inbound security rules that will control access.
Access the Database Dashboard:
-
-
- Log in to the AWS Management Console.
- Navigate to the RDS service by selecting “RDS” under “Database” services or searching for RDS in the service search bar.
- Click on “Databases” in the left-hand navigation pane to view a list of your database instances.
Select Your Database Instance:
-
-
- From the list of databases, click on the “DB Identifier” of the database instance you wish to make publicly accessible. This action will take you to the database’s details page, which provides an overview of your database’s configurations, status, and connectivity options.
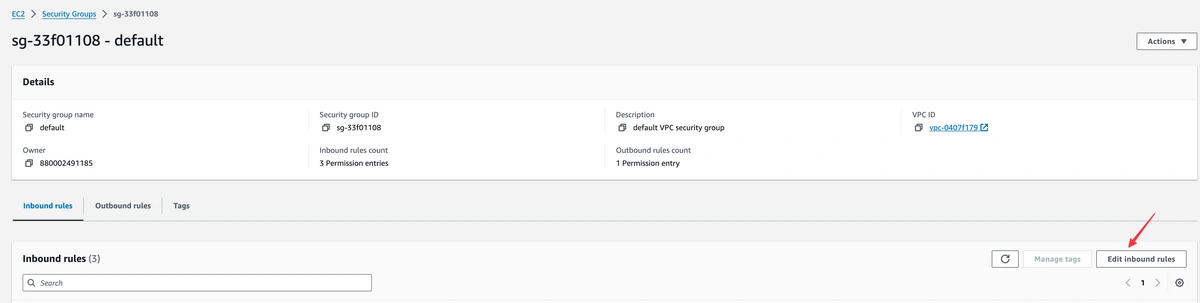
Modify the Database Instance:
-
-
- Look for the “Modify” button, typically located at the top of the database details page. Clicking on “Modify” will allow you to change various settings of your database instance.
See the screenshow below for reference:
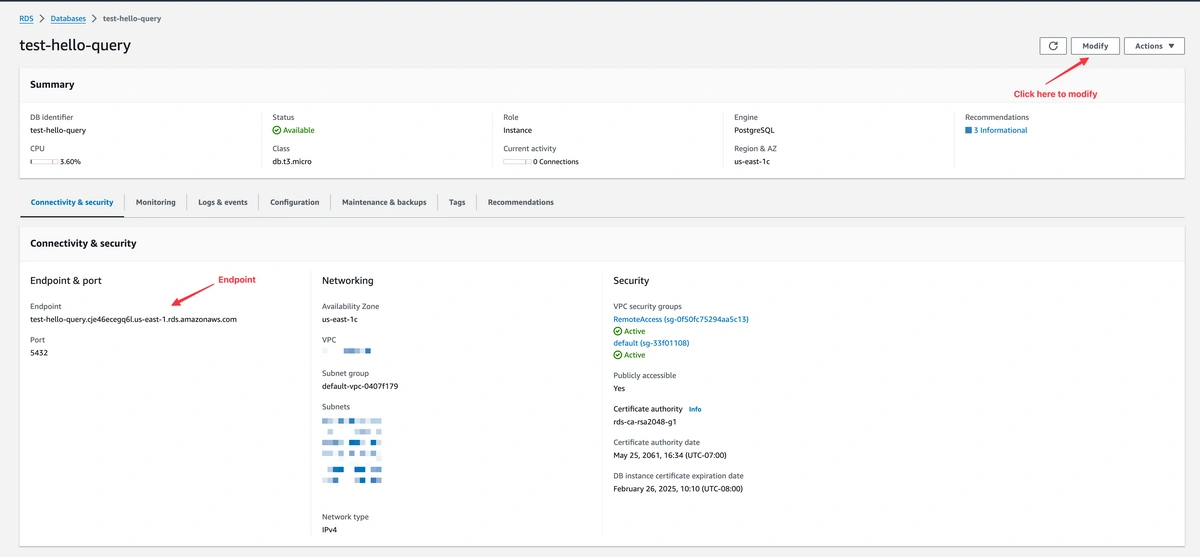
Next, click on “Additional configuration”
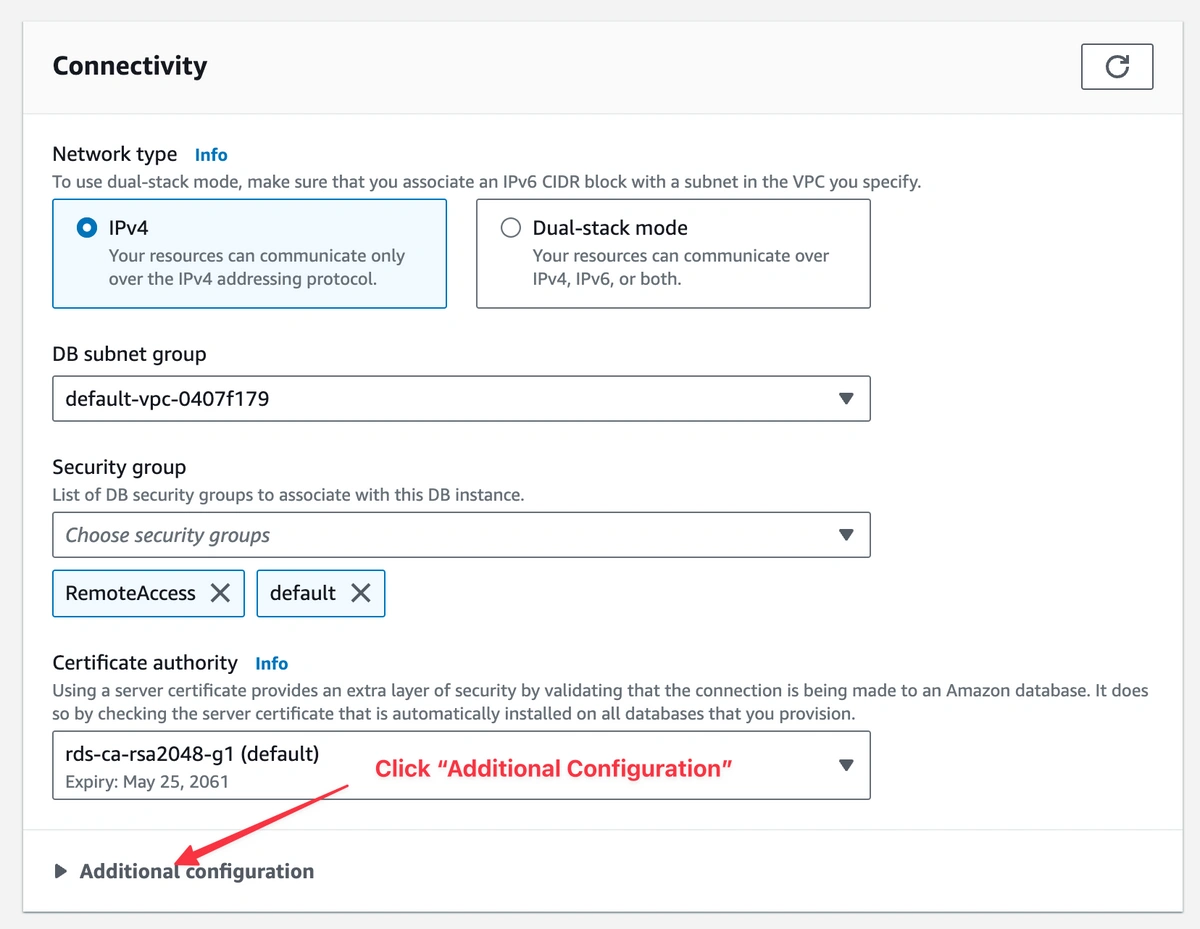
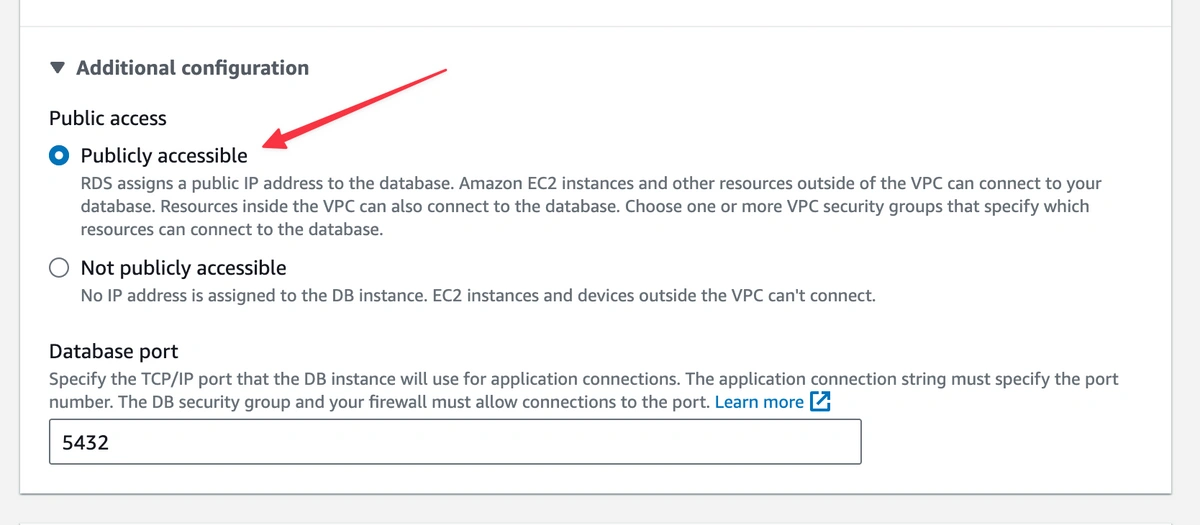
Next select “Publicly Accessible”. Click on “Continue” and then “Save”.
Create Inbound Security Rules
Next you’ll need to edit the inbound security rules of your database's VPC security group. If the database instance was created in a VPC, it must have a VPC security group that authorizes connections.
Should you encounter any difficulties or require additional information, AWS provides comprehensive documentation on this topic, available at AWS RDS Security Group Documentation.
You can modify your existing security group or create a new one. From your database page, click on your security group as shown in the screenshot below.
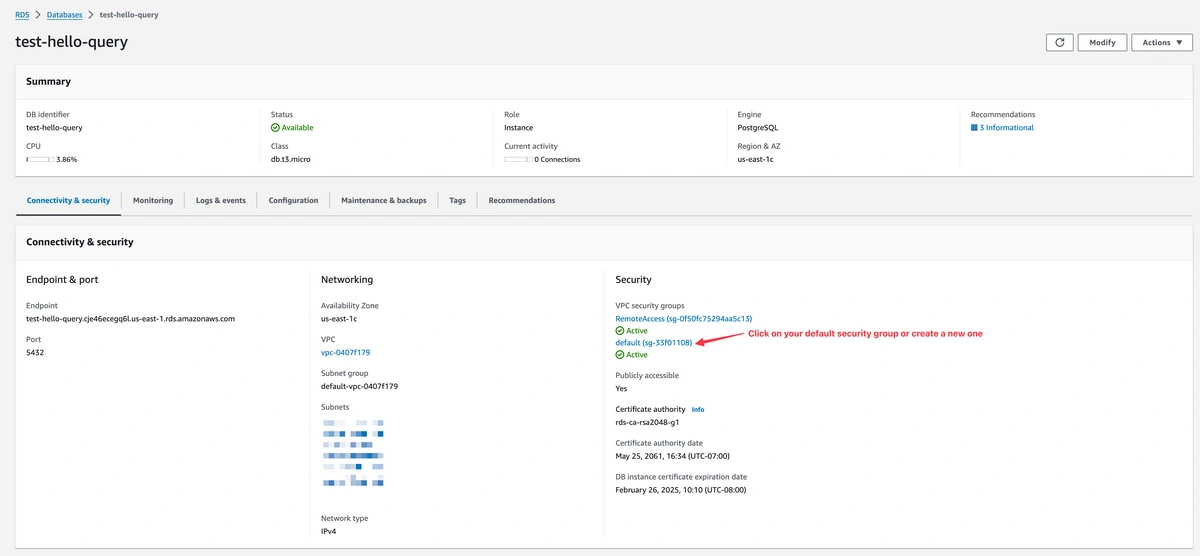
Continue to click through to your security group ID.
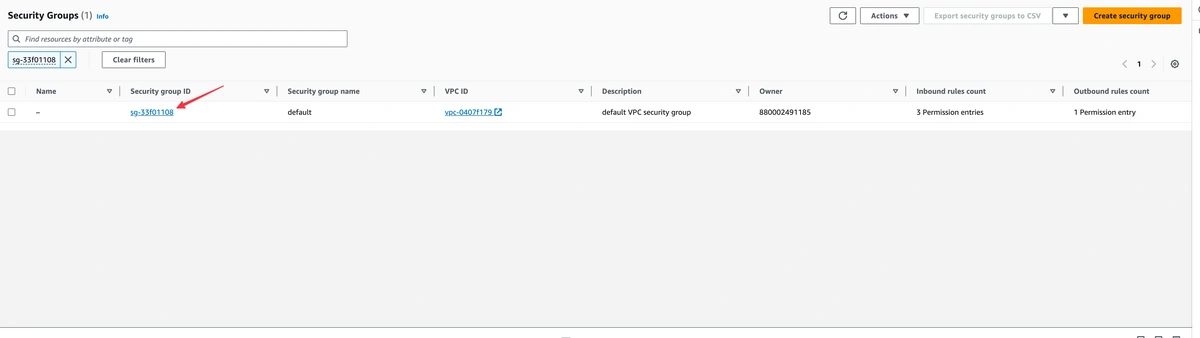
Click on “Edit Inbound Rules”
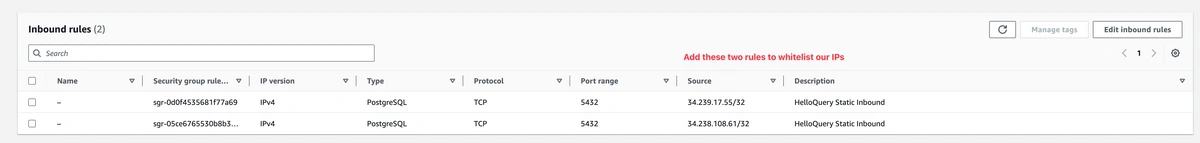
Whitelisting HelloQuery's Static IP Addresses
In the security group section you need to add the HelloQuery IPs.
Add Whitelist Rules:
-
-
- Click on “Add rule” for each HelloQuery IP address (there are two).
- Set the “Type” to “PostgreSQL” for each rule, ensuring the port remains set to 5432.
- In the “Source” field, input HelloQuery’s static IP addresses individually:
34.238.108.61/32 and 34.239.17.55/32. The /32 suffix denotes a single IP address.
Finalize the Rules:
-
-
- After adding the rules, click “Save Rules” to save the changes.
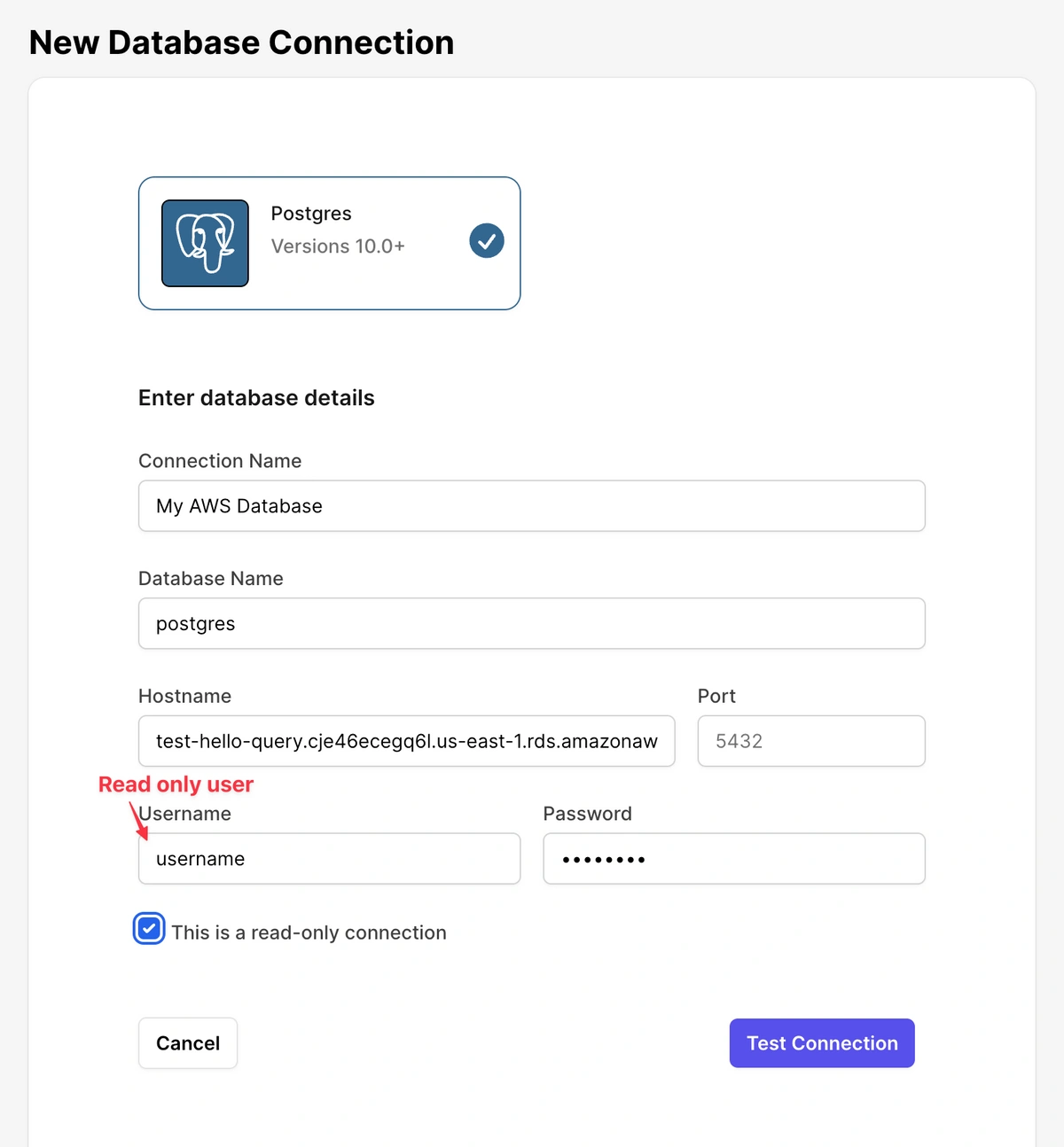
Test HelloQuery Connection
After configuring the inbound security rules in your AWS RDS security group, the next step is to verify that HelloQuery can successfully connect to your AWS RDS instance. This preliminary test ensures that the credentials and network configurations are correctly set up for a secure connection.
Sign In to HelloQuery:
Configure a Test Connection:
-
-
- Enter your credentials as shown in the screenshot below.
Click “Test Connection”:
-
-
- With the details entered, proceed to "create and test" the connection. This step does not yet involve any data exchange but verifies the ability of HelloQuery to reach and authenticate with your AWS RDS database.
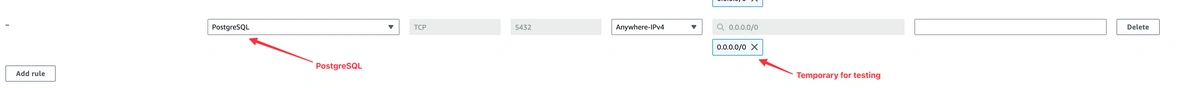
Troubleshooting - Temporarily Allow All IP Addresses (only do this if you can't connect)
If you are having issues connecting, you can temporarily allow all IP addresses to access your database to figure out the problem. If you cannot connect successfully with 0.0.0.0 inbound there is an error in your credentials. If you can, there's an error with the whitelisting. Please reach out to [email protected] for assistance.
Note: This step is for testing purposes only and should be reversed after the test to maintain security.
Add a New Inbound Rule:
- Within the security group's “Inbound rules” tab, click on “Add rule” to create a new entry.
- For “Type,” select “PostgreSQL.” This selection will automatically set the port to 5432, which is the default for PostgreSQL databases.
- In the “Source” field, enter
0.0.0.0/0 to temporarily allow all IP addresses. This setting will enable you to test the connectivity without IP restrictions.
Apply the Rule:
- Click on “Save Rules” to save this new inbound rule.
Final Security Measures
- Revoking Temporary Access:
- Once you’ve connected with your new connection details, delete the Security Rule allowing Postgres access via
0.0.0.0
Get Started with HelloQuery
Your AWS RDS instance is securely connected, and you're ready to use HelloQuery. Dive into data analysis and management with confidence, knowing our support team is here if you need us. Thank you for choosing HelloQuery. Let the report building begin!